In the world of distributed computing and blockchain, achieving consensus among nodes is a critical challenge—especially in the presence of malicious actors or system failures. One of the most robust solutions to this challenge is Practical Byzantine Fault Tolerance (PBFT), a consensus algorithm designed to function efficiently even when some nodes behave unpredictably or maliciously.
Originally proposed in the late 1990s, PBFT has gained renewed attention with the rise of blockchain networks and decentralized applications (dApps). In this article, we’ll break down what Practical Byzantine Fault Tolerance is, how it works, its benefits and limitations, and where it fits within the broader ecosystem of consensus protocols.
What Is Practical Byzantine Fault Tolerance?
Practical Byzantine Fault Tolerance (PBFT) is a consensus algorithm designed to solve the Byzantine Generals Problem—a classic dilemma in distributed computing that deals with reaching agreement in the presence of faulty or malicious nodes.
The term “Byzantine” refers to the possibility of nodes not only failing but doing so in a deceptive or unpredictable manner. PBFT provides a practical solution by allowing a distributed system to reach consensus even if up to one-third of the nodes are faulty or malicious.
PBFT is deterministic, meaning it ensures finality—once a decision is made, it cannot be reversed. This makes it well-suited for applications that require strong consistency guarantees, such as financial systems and enterprise blockchains.
How Practical Byzantine Fault Tolerance Works
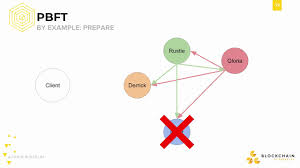
The PBFT algorithm follows a three-phase protocol—pre-prepare, prepare, and commit—designed to confirm the validity of a request and agree on the outcome across a network of nodes.
Here’s a high-level overview of how it works:
- Client Request
A client sends a request (e.g., a transaction) to the primary node (also known as the leader). - Pre-Prepare Phase
The primary assigns a sequence number to the request and multicasts a pre-prepare message to the replica nodes (secondary nodes). - Prepare Phase
Each replica verifies the message and broadcasts a prepare message to all other nodes. - Commit Phase
Upon receiving a sufficient number of matching prepare messages, nodes send a commit message. When a node receives enough commit messages (typically 2f + 1 out of 3f + 1), it executes the request and sends the result back to the client. - Client Confirmation
The client waits to receive f + 1 matching replies from different nodes, which confirms the operation is committed.
This process ensures that all honest nodes agree on the same state, even if up to f nodes are malicious.
Key Benefits of PBFT
- Byzantine Fault Tolerance
PBFT can handle malicious nodes without compromising consensus, making it ideal for adversarial environments. - Low Latency
Unlike Proof of Work (PoW), PBFT does not require energy-intensive computations, allowing for faster transaction finality. - Strong Consistency
Once a transaction is committed, it is final and cannot be reversed—eliminating the risk of forks. - Energy Efficient
PBFT doesn’t rely on mining, making it far more environmentally friendly compared to PoW-based systems like Bitcoin. - High Throughput in Small Networks
PBFT can process hundreds or even thousands of transactions per second in smaller or permissioned networks.
Limitations of PBFT
- Scalability Issues
PBFT requires all-to-all communication among nodes, which becomes inefficient as the number of nodes increases. Its communication complexity is O(n²), making it less suitable for large public blockchains. - Vulnerability to DoS Attacks on Leader
If the primary node is targeted by a Denial of Service (DoS) attack, it can disrupt the entire consensus process. Although view-change protocols exist to elect a new leader, this adds latency. - Trust Assumptions
PBFT assumes that fewer than one-third of the nodes are malicious. If this threshold is exceeded, the system may fail to reach consensus. - Limited Adoption in Open Networks
Due to its scalability constraints, PBFT is mostly used in permissioned (private) blockchains like Hyperledger Fabric and Tendermint, rather than in open, public networks.
Real-World Applications of PBFT
PBFT is especially well-suited for enterprise-grade blockchain applications that prioritize security and consistency over decentralization.
- Hyperledger Fabric: One of the most prominent enterprise blockchain frameworks, Fabric implements a PBFT-inspired consensus mechanism for permissioned environments.
- Zilliqa: A high-throughput blockchain platform that uses PBFT in combination with sharding.
- Tendermint: A BFT-based consensus engine used in the Cosmos network, designed for interoperability between blockchains.
PBFT vs. Other Consensus Algorithms
| Feature | PBFT | PoW (Bitcoin) | PoS (Ethereum) |
|---|---|---|---|
| Finality | Immediate | Probabilistic | Deterministic (now) |
| Energy Efficiency | High | Low | High |
| Throughput | High (small networks) | Low | Medium to High |
| Scalability | Limited | Moderate | Better than PBFT |
| Use Case | Permissioned networks | Public networks | Public networks |
Conclusion
Practical Byzantine Fault Tolerance remains a foundational consensus algorithm in distributed systems, offering strong guarantees of safety, consistency, and fault tolerance. While not ideal for large-scale public blockchains due to scalability issues, PBFT excels in permissioned environments where node identities are known and trust can be semi-established.
As the blockchain ecosystem matures, hybrid approaches combining PBFT with other consensus mechanisms are emerging, aiming to harness the strengths of multiple models. Understanding PBFT is crucial for developers, architects, and investors looking to navigate the increasingly complex world of decentralized technologies.








Leave A Reply