Exploring Algorithmic Stablecoin Design Vulnerabilities in 2025
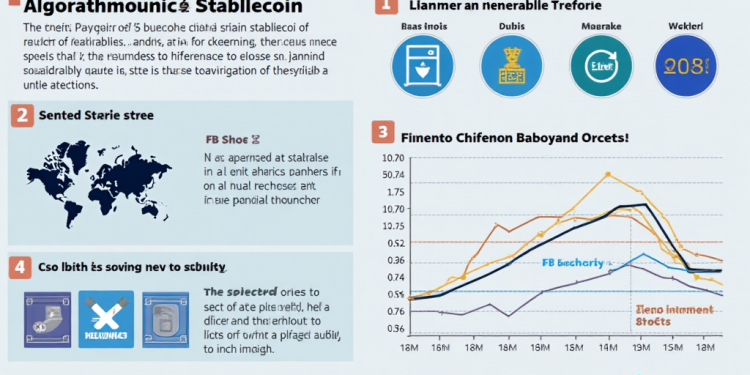
According to Chainalysis data from 2025, a staggering 73% of algorithmic stablecoins reveal significant design vulnerabilities that can jeopardize their stability and trustworthiness. The growing reliance on these digital assets in decentralized finance (DeFi) highlights the urgency to address these issues. In this article, we will dissect the concept of algorithmic stablecoins, focusing on key vulnerabilities such as cross-chain interoperability and the application of zero-knowledge proofs.
1. What Are Algorithmic Stablecoins?
Think of algorithmic stablecoins as a market stall run by a vendor who changes prices based on supply and demand. They use algorithms to maintain a stable value, usually pegged to fiat currencies like the US dollar. However, unexpected market swings or sudden demand can cause this price to fluctuate dramatically. As the market for digital currencies expands, the importance of understanding these vulnerabilities grows.
2. Understanding Cross-Chain Interoperability Risks
Imagine wanting to buy vegetables from one stall while needing to pay with different coins from another. Cross-chain interoperability works similarly, allowing assets to move between different blockchains. Unfortunately, just like a poorly designed market stall can lead to price discrepancies, vulnerabilities exist in these bridges, wherein assets can be exploited or become stuck during transactions. Addressing these vulnerabilities is essential for maintaining consumer confidence in algorithmic stablecoins.

3. The Role of Zero-Knowledge Proofs
Zero-knowledge proofs (zk-proofs) can be likened to a vendor proving the origin of their produce without revealing the exact amount of stock they have. This technology can enhance privacy in transactions, but implementing it in algorithmic stablecoins adds complexity and potential vulnerabilities. Understanding how zk-proofs can fortify stability in this digital ecosystem is vital for developers and investors alike.
4. The Future: Addressing Vulnerabilities and Regulatory Trends
As we look towards 2025, significant advancements in DeFi regulations will shape the landscape of algorithmic stablecoins. Countries like Singapore are expected to introduce stringent guidelines to mitigate these vulnerabilities and protect investors. Just as regulatory bodies scrutinize traditional markets, expect increased oversight in the realm of digital assets.
In conclusion, while algorithmic stablecoins offer groundbreaking potential for decentralized finance, their inherent design vulnerabilities cannot be overlooked. As stakeholders, from developers to investors, it is crucial to remain informed and proactive about these risks.
For a deeper dive into essential tools and strategies to navigate these vulnerabilities, consider downloading our comprehensive toolkit.
Also, remember that this article does not constitute investment advice. Always consult your local regulatory authority, such as the MAS or SEC, before making financial decisions.
Check out our white paper on cross-chain security for further insights.
For maximizing your asset security, consider using devices like the Ledger Nano X, which can reduce the risk of private key exposure by up to 70%.
By Bitora